SaintCon was amazing this year. If you aren’t familiar with SaintCon, it’s the premier internet security conference in Utah. I would contend that its one of the best in the country. At SaintCon there is always a hackers challenge (CTF). I’m going to go over some of the challenges so someone can learn the things I learned.
Binary challenge 1
A pretty straight forward challenge. We were given a binary to download. All it took was running ‘strings’ on the binary.
$ strings -a thread_edebd39bb52183389cd8f153b3ba25e1
Which resulted in the output:
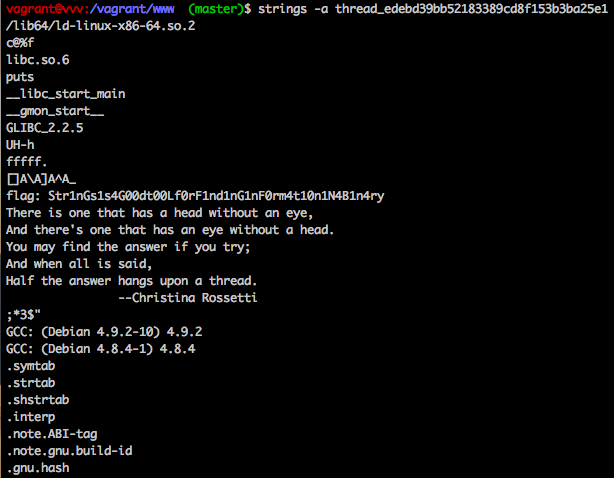
As you can see, this grabbed all readable text from the binary and dumped it. The flag was in there followed by a quote.
Binary challenge 2
The title of this binary was “crashme”. To look for clues I ran strings on this file as well:
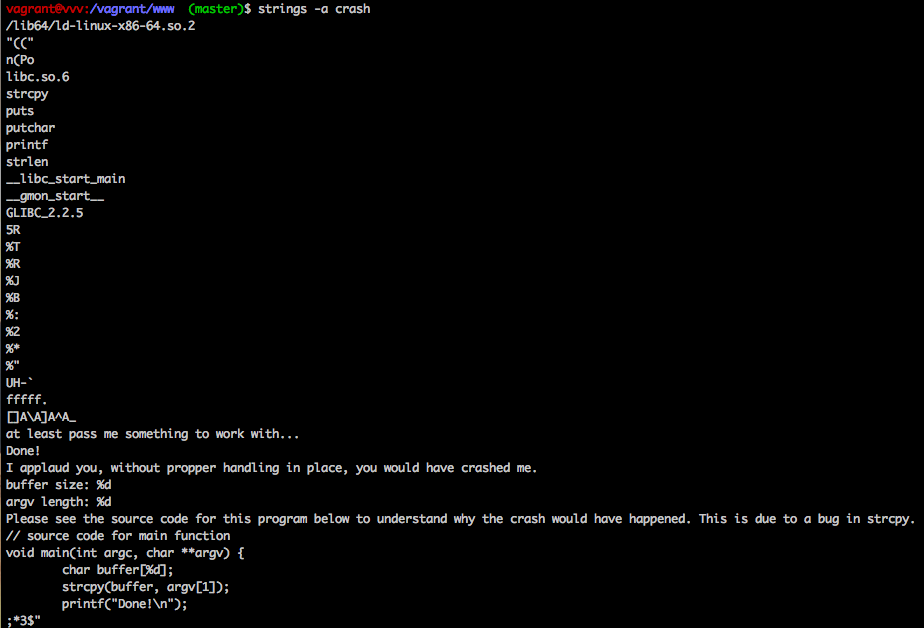
After looking into strcpy(), it was apparent that it was easy to accidentally allow a buffer overflow. We could easily test a 100,000 character buffer with a simple command.
$ ./crash $(python -c "print 'A'*100000")
Which produced the output:
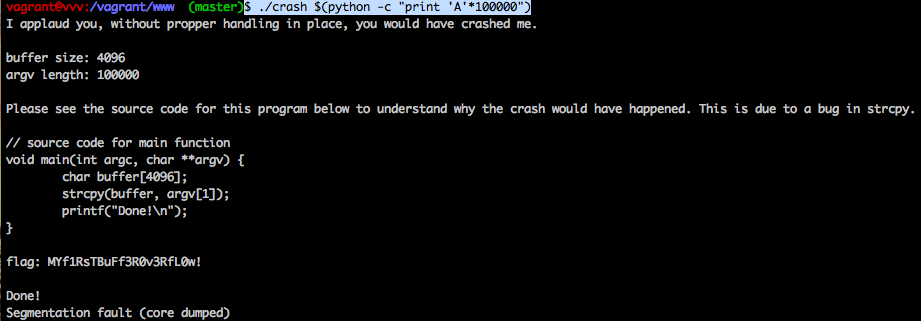
After the buffer overflow, we had retrieved the flag.
Potent Pwnables last challenge
This was one of my favorite challenges. This was pretty much an exact replication of the latest Joomla! session hijacking vulnerability. There were a number of changes such as the database prefix being different and the page_id/item_id being different, but those were trivial to find out once it was identified.
The tool that made this challenge easier is called hackbar. It makes editing your SQL injection a lot easier than in the url bar. For more information on this exploit, I suggest reading the Proof of Concept linked to earlier.
I’ll get some more challenges up as I have time. Thanks for reading.